Evading EDR The Definitive Guide to Defeating Endpoint Detection Systems
by Matt Hand
No Starch Press, 2024
https://nostarch.com/evading-edr
| Page | Remark |
|---|---|
| x | network compromises are inevitable |
| xx | stop treating security tools like magic boxes |
| xxiii | Visual Studio |
| Windows Driver Kit (WDK) | |
| WinDbg | |
| Ghidra | |
| Sysinternals | |
| Cobalt Strike | |
| Mythic | |
| Covenant | |
| 1 | telemetry |
| 2 | agent, EDR |
| Security Incident and Event Management (SIEM) | |
| 3 | sensors, EDR |
| performance of EDR sensors | |
| 4 | detections |
| EDR evasions - challenges of | |
| 5 | EDR bypass |
| Security Operations Center (SOC) | |
| identifying malicious activity | |
| 6 | context |
| 7 | brittle vs. robust detections |
| mimikatz | |
| filename-dased detection - mimidogz.exe | |
| false positive | |
| 8 | Elastic Detection Rules |
| Bifrost | |
| Kerberoasting | |
| Command-line based detections | |
| 9 | Atomic Test Harnesses - Red Canary |
| EDR agent design | |
| basic design: static scanner, hooking dll, kernel driver, agent service | |
| intermediate design: network filter driver, filesystem filter driver, etw consumer, Early Launch Antimalware (ELAM) | |
| advanced design: hypervisors, deception | |
| 12 | types of bypasses: configuration, perceptual, logical, classification |
| 18 | function hooking |
| System Service Dispatch Table (SSDT) | |
| 19 | Kernel Patch Protection (KPP) |
| PatchGuard | |
| ntdll.dll commonly hooked functions | |
| Microsoft Detours | |
| 22 | AppInit DLLs |
| Kernel Asynchronous Procedure Call (KAPC) | |
| detection function hooks | |
| 23 | Restricted User Mode |
| Hypervisor Code Integrity | |
| 24 | evading function hooks |
| blocking non-Microsoft signed DLLs | |
| Vectored Exception Handler (VEH) | |
| 25 | Direct syscalls |
| Microsoft Macro Assembler (MASM) | |
| 26 | SysWhispers |
| 27 | dynamically resolving syscall numbers |
| “Bypassing User-Mode and Direct Invocation of System Calls for Red Teams” https://www.mdsec.co.uk/2020/12/bypassing-user-mode-hooks-and-direct-invocation-of-system-calls-for-red-teams/ | |
| modexpblog https://modexp.wordpress.com/ | |
| 28 | remapping ntdll.dll |
| 29 | Sysmon |
| 30 | percentage of processes injecting ntdll.dll |
| remapping ntdll.dll into a new suspended process | |
| 33 | notification callback routines |
| 35 | register a process callback routine |
| 36 | PsCreateProcess notify subsystems |
| Windows Subsystem for Linux (WSL) | |
| 38 | Sysmon Event ID 1 - Process creation |
| 39 | thread notifications |
| thread callback routine | |
| PsSetCreatThreadNotifyRoutine | |
| 40 | detecting remote thread creation |
| 41 | Sysmon Event ID 9 - Thread creation |
| Windows Error Reporting (WER) - werfault.exe | |
| Command Line Tampering | |
| 42 | PEB w/ WinDbg |
| “How to Argue Like Cobalt Strike” https://blog.xpnsec.com/how-to-argue-like-cobalt-strike/ | |
| Process Hacker | |
| GMER | |
| 43 | NtQueryInformationProcess |
| 44 | PROCESS_BASIC_INFORMATION |
| 45 | PPID spoofing |
| 46 | STARTUPINFOEX struct |
| PROC_THREAD_ATTRIBUTE_PARENT_PROCESS | |
| 48 | DbgView |
| “Detecting Parent PID Spoofing - F-Secure https://blog.f-secure.com/detecting-parent-pid-spoofing/ | |
| ETW | |
| 49 | Process-Image Modification |
| application whitelisting bypassing | |
| 50 | hollowing |
| 51 | doppelganging |
| “Lost in Transaction: Process Doppelganging https://www.youtube.com/watch?v=XmWOj-cfixs | |
| https://www.blackhat.com/docs/eu-17/materials/eu-17-Liberman-Lost-In-Transaction-Process-Doppelganging.pdf | |
| Transactional NTFS (TxF) | |
| 52 | Herpaderping |
| Process Ghosting | |
| 53 | detecting process image modification |
| 56 | Pico - minimal processes |
| Virtual Address Descriptor (VAD) | |
| Blackbone | |
| 58 | fork&run |
| 59 | Cobalt Strike, Beacon, malleable profiles, execute-assembly, Beacon Object Files (BOFs) |
| 61 | objects: files, processes, tokens, registry keys, … |
| object notifications | |
| 63 | monitoring new and duplicate process handle requests |
| 64 | detecting objects monitored by EDR |
| 65 | callback list - OBJECT_TYPE |
| CALLBACK_ENTRY_ITEM | |
| preoperation CALLBACK_ENTRY_ITEM | |
| 66 | WdFilter.sys |
| Windows Defender | |
| 68 | evading object callbacks |
| mimikatz | |
| ProcDump | |
| 69 | access mask fingerprinting |
| handle theft | |
| 74 | race conditions |
| “Fast and Furious: Outrunning Windows Kernel Notification Routines” https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7338165/ | |
| 76 | PID guessing |
| 79 | image load nofication |
| registry notification | |
| KAPC injection | |
| 80 | clr.dll |
| 84 | Metasploit Framework |
| 85 | bastion host |
| proxychains | |
| Proxifier | |
| 86 | gTunnel |
| triggering KAPC injection | |
| APC injection | |
| 90 | preventing KAPC injection |
| 91 | attestation-signed by Microsoft |
| Arbitrary Code Guard (ACG) | |
| registry notifications | |
| 92 | service hijacking |
| registering a registry notification | |
| 95 | performance issues with EDR |
| 96 | evading registry callbacks |
| 100 | callback entry overwrites - EDR evasion |
| 100 | MimiDrv |
| 101 | Hypervisor-Protected Code Integrity (HVCI) |
| 103 | minifilter |
| ntfs.sys | |
| npfs.sys | |
| 104 | “Understanding Minifilters: Why and How File System Filters Evolved” https://www.osr.com/nt-insider/2019-issue1/the-state-of-windows-file-system-filtering-in-2019/ |
| filter drivers - legacy | |
| 105 | filter manager (fltmgr.sys) |
| 106 | minifilter architecture |
| minifilter altitude | |
| 107 | FSFilter anti-virus |
| FSFilter activity monitor | |
| 108 | writing a minifilter |
| altitudes of popular EDR minifilters | |
| 115 | managing a minifilter |
| INF files | |
| 116 | sc.exe |
| Service Control API | |
| filter manger FltLib | |
| detecting adversaries with minifilters | |
| tradecraft | |
| file detections | |
| 117 | named pipe detections |
| Mojo (Chromium) | |
| 118 | “Detecting Cobalt Strike Default Modules via Named Pipe Analysis” https://labs.withsecure.com/publications/detecting-cobalt-strike-default-modules-via-named-pipe-analysis |
| OPSEC | |
| evading minifilters | |
| fltmc.exe | |
| 119 | File Manager Event ID 1 - filter unloaded |
| 123 | network filter drivers |
| Windows Filtering Platform (WFP) | |
| 124 | Network Intrusion Detection System (NIDS) |
| endpoint-based traffic monitoring | |
| 125 | network driver interface specification |
| types of network drivers: miniport, protocol, filter, intermediate | |
| 126 | Windows Filtering Platform (WFP) |
| tcpip.sys - ipv4 | |
| tcpip6.sys - ipv6 | |
| 127 | filter engine |
| filter arbitration | |
| 128 | callout drivers |
| WFP callout driver implementation | |
| 134 | Security Descriptor |
| 135 | detecting adversary tradecraft with network filters |
| 139 | network filter evasion |
| 140 | NtObjectManager |
| 143 | Event Tracing for Windows (ETW) |
| printf-based debugging | |
| 144 | GUID |
| 145 | Security Descriptor |
| 146 | Managed Object Format (MOF) |
| Windows Software Trace Preprocessor (WPP) | |
| Manifests | |
| XML | |
| TraceLogging | |
| 147 | find ETW provider image |
| 149 | controllers |
| logman.exe | |
| 151 | Consumers |
| .NET assemblies | |
| class names of offensive tools | |
| 165 | evading ETW-based detections |
| “Tampering with Windows Event Tracing: Background, Offense, and Defense” https://blog.palantir.com/tampering-with-windows-event-tracing-background-offense-and-defense-4be7ac62ac63 | |
| patching | |
| configuration modification | |
| 166 | trace-session tampering |
| trace-session interference | |
| bypassing a .NET consumer | |
| “Hiding your .NET ETW” https://blog.xpnsec.com/hiding-your-dotnet-etw/ | |
| SharpHound | |
| BloodHound | |
| 169 | “Universally Evading Sysmon and ETW” https://blog.dylan.codes/evading-sysmon-and-windows-event-logging/ |
| Kernel Driver Utility (KDU) | |
| driver signature enforcement | |
| infinity hook | |
| 170 | Task Scheduler |
| 171 | scanners |
| 172 | Vienna virus |
| Bernd Fix | |
| F-PROT - FRISK | |
| anti-virus | |
| Veil | |
| 173 | on-demand scanning |
| on-access scanning | |
| real-time-protection | |
| 174 | ransomware |
| bcdedit.exe | |
| VirusTotal | |
| FIN7 | |
| YARA | |
| 175 | YARA rules |
| Safetykatz | |
| 179 | evading scanner signatures |
| dnSpy | |
| DefenderCheck | |
| 181 | base64 |
| P/Invoke | |
| D/Invoke | |
| Rubeus | |
| 183 | Antimalware Scan Interface (AMSI) |
| fileless malware | |
| 184 | Living off the Land |
| Empire | |
| 185 | download cradle |
| invoke-expression | |
| 186 | Microsoft Defender IOfficeAntivirus |
| MpOav.dll | |
| whoamsi - Duane Michael | |
| PowerShell | |
| JavaScript | |
| VBScript | |
| Windows Script Host | |
| Office VBA Macros | |
| User Account Control (UAC) | |
| System.Management.Automation.dll | |
| 187 | AmsiUtils.ScanContent() |
| AmsiUtils.WinScanContent() | |
| European Institute for Computer Antivirus Research (EICAR) | |
| 189 | COM class factory |
| 190 | Control Flow Guard |
| 193 | Implementing a Custom AMSI provider |
| 194 | Windows runtime C++ template library |
| 196 | evading AMSI |
| 197 | string obfuscation |
| AMSI patching | |
| amsi.dll | |
Matt Graeber AMSI patching Tweet 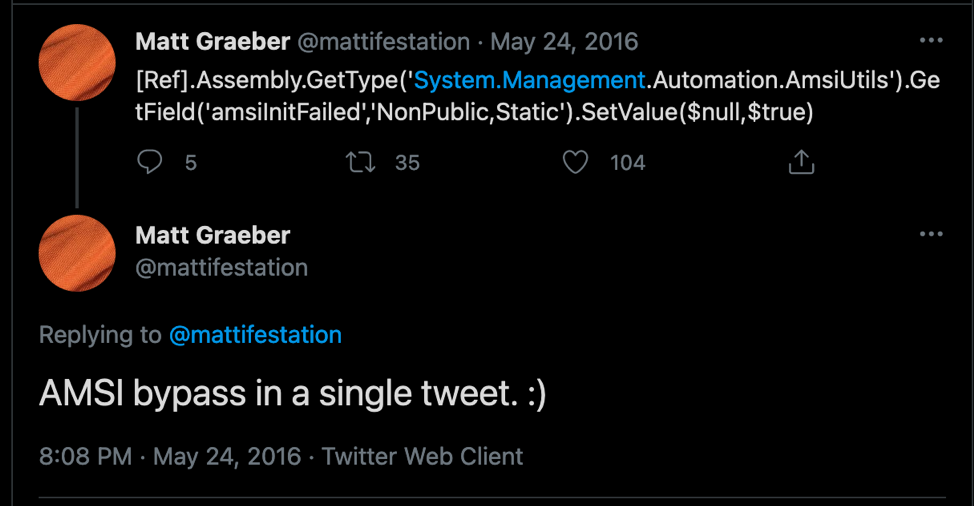 |
|
| https://news.sophos.com/en-us/2021/06/02/amsi-bypasses-remain-tricks-of-the-malware-trade/ | |
| 198 | “Memory Patching AMSI Bypass” https://rastamouse.me/memory-patching-amsi-bypass/ |
| 199 | Ceri Coburn AMSI bypass |
| 201 | Zacinlo adware |
| Detrahere malware family | |
| self-protection | |
| shutdown handlers | |
| Cacinlo rootkit | |
| boot-start driver | |
| 202 | Early Launch Anti Malware (ELAM) |
| Trusted Boot | |
| Microsoft Virus Initiative | |
| production driver | |
| 203 | developing ELAM drivers |
| 208 | makecert.exe |
| signtool.exe | |
| 210 | RFC-3161 - Time Stamp Protocol |
| 211 | System Guard runtime monitor |
| sgrmagent.sys | |
| winload.efi | |
| 212 | evading ELAM drivers |
| “Understanding WdBoot” https://n4r1b.com/posts/2019/11/understanding-wdboot-windows-defender-elam/ | |
| driver signature enforcement | |
| Extended Validation (EV) certificate | |
| Windows Hardware Quality Labs (WHQL) | |
| Windows Update | |
| Bring Your Own Vulnerable Driver (BYOVD) | |
| firmware rootkits | |
| bootkits | |
| ESpecter bootkit | |
| 213 | bootmgfw.efi |
| UEFI | |
| “Rootkits and Bootkits: reversing modern malware and next-generation threats” https://nostarch.com/rootkits | |
| 215 | Microsoft-Windows-Threat-Intelligence ETW provider (EtwTi) |
| 219 | PerfView.exe |
| 221 | neo4j |
| 222 | graph theory - edges and nodes |
| Structured Query Language (SQL) | |
| Active Directory | |
| Microsoft Azure | |
| Cypher query language | |
| “Intro to Cypher” https://blog.cptjesus.com/posts/introtocypher/ | |
| JSON | |
| CallTreeToJSON.py Ghidra script | |
| Ghidra Script Manager | |
| 226 | Secure ETW |
| 227 | DRM |
| Protected Process Light (PPL) | |
| 229 | Enhanced Key Usage (EKU) |
| 230 | New-SelfSignedCertificate PowerShell cmdlet |
| .pfx file format | |
| certmgr.exe | |
| 234 | evading EtwTi |
| 235 | “Data Only Attack: Neutralizing EtwTi Provider” https://public.cnotools.studio/bring-your-own-vulnerable-kernel-driver-byovkd/exploits/data-only-attack-neutralizing-etwti-provider |
| atillk64.sys - Gigabyte | |
| lha.sys - LG Device Manager | |
| 240 | Excel Add-In (XLL) |
| xlAutoOpen() | |
| xlAutoClose() | |
| 242 | global uniqueness |
| 244 | command and control |
| Unique Resource Identifier (URI) | |
| 245 | Virtual Private Server (VPS) |
| LetsEncrypt | |
| jitter | |
| 246 | persistence |
| 247 | MITRE ATT&CK |
| China’s Ministry of State Security (MSS) | |
| known unknowns | |
| shell preview handlers | |
| “Life is Pane: Persistence via Preview Handlers” https://medium.com/@matterpreter/life-is-pane-persistence-via-preview-handlers-3c0216c5ef9e-b73a9515c9a8 | |
| 249 | reconnaissance |
| Seatbelt | |
| child process creation | |
| abnormal module loading | |
| 250 | tool-specific indicators; toolmarks |
| reflection | |
| privilege escalation | |
| 251 | LSASS |
| LogonEvents | |
| C:\Users\ | |
| .lnk file backdoors | |
| hijacking file handlers | |
| HKU:\<SID>\Software\Classes - per user | |
| 252 | HKLM:\Software\Classes - system-wide |
| Set-FileAssoc.ps1 | |
| 253 | psinject |
| 254 | environmental keying |
| 255 | AES256 |
| tamper sensor | |
| 256 | LLVM |
| ProtID (COM) | |
| 258 | lateral movement |
| 260 | SMB |
| enumerating shares | |
| C$ | |
| 261 | System Access Control List (SACL) |
| Event ID 4663 | |
| 262 | file exfiltration |
| fault tolerance | |
| 265 | alternative hooking methods |
| 266 | “Esoteric Hooks” https://github.com/ionescu007/HookingNirvana/blob/master/Esoteric%20Hooks.pdf |
| Hooking Nirvana | |
| RPC filters | |
| PrinterBug | |
| PetitPotam | |
| 267 | DCSync |
| netsh.exe | |
| Directory Replication Service | |
| 268 | Event ID 5157 |
| 269 | hypervisors |
| rings | |
| ring 3 - user-mode | |
| ring 0 - kernel | |
| Virtual Machine Control Structure (VMCS) | |
| Intel VT-x | |
| VMEXIT | |
| RDMSR | |
| VMRESUME | |
| Type-1 hypervisor | |
| 270 | Type-2 hypervisor |
| VirtualBox | |
| VMWare Workstation | |
| “Full hypervisor Implemention” https://github.com/SinaKarvandi/Hypervisor-From-Scratch | |
| virtual machine detection | |
| 271 | syscall interception |
| Extended Feature Enable Register (EFER) | |
| Control Register Modification | |
| Memory Change Tracing | |
| Extended Page Tables (EPT) | |
| branch tracing | |
| evading hypervisors |